Late last year I saw an unexpected UX failure when adding a new Microsoft Authenticator app as the MFA method. It appears that a few months later the issue still persists.
Azure / EntraID MFA
MFA methods offered by MS Azure / Entra ID
Azure / EntraID supports the expected 6 digit MFA codes via SMS or OTP app. These are the typical solutions. There are also various more complex options that require additional configuration such as FIDO2 and certificate based authentication.
The full current list of supported MFA methods can be found here.
There is one more prominent and easy to set up MFA option, the Microsoft authenticator app.
MFA User Experience and loss of 2nd factor
Once set up, using MFA with MS365 services is very straightforward. However, power users will often have an immediate concern about loss of the authenticator. The typical set up will rely on SMS codes sent to a mobile phone, or a TOTP MFA app (on the same phone). With MS365 services, Microsoft Authenticator is also an option, and is again tied to the same phone.
As such, losing the phone leads to a service lockout and support calls.
Once a user experiences this, they may decide to preemptively avoid it and register a second phone for SMS, or a second TOTP app. In a self service scenario, the user would also want to add a second device if replacing their old one, and to avoid lockout issues they may want to register the second device before removing the first.
Additional MFA device user experience
Adding an additional device to receive SMS is very straightforward, as is adding a new device with a TOTP app.
Adding a new Microsoft Authenticator app may be expected to be a similar process, and one may assume it should just work.
From a user perspective, there's no reason to stop and consider if it is or indeed should be possible to run two or more copies of MS Authenticator. After all, Apple's proprietary MFA built-in to iOS can and does prompt the user on all of their devices at once and keeps the state synchronised.
The MFA management portal shows no errors if a user tries to add an additional MS Authenticator.
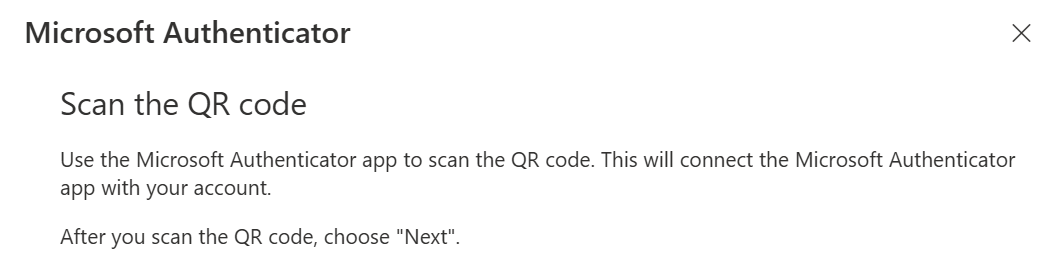
However, the next step of adding the authenticator will not happen.
Instead, the process halts with an unexpected timeout error.
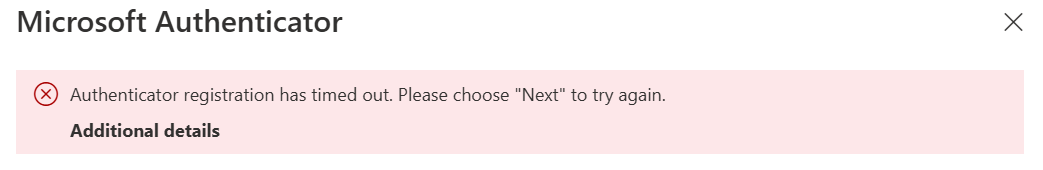
It's possible to re-attempt the process, and the outcome does not change.
Note that there is no indication to the user that the problem is their existing MS authenticator app.
Resolution
While unexpected, the resolution is as follows:
When adding a backup/replacement authenticator device, add only a new TOTP app (non-MS Authenticator), or SMS (noting that SMS is generally considered insecure and should be used when no other options are available).
Adding MS Authenticator should only be done after deleting the existing MS Authenticator app as trying to add it twice leads to the timeout errors shown above.