As of the end of June 2023 March 2024, Powershell modules AzureAD, AzureADPreview, and MSOnline will be deprecated. The provided replacement is Microsoft Graph Powershell.
However, you may be surprised to find out just what's required in order to get it working, and may find that you need to re-evaluate your Powershell automation projects.
Scope of the changes
This change only affects MSOline/AzureAD Powershell modules - that is, scripting support for AzureAD-related tasks such as user management, licensing, MFA status, and other MS365 features.
This does not impact the CLI options for managing Azure workloads, that is, Azure CLI and the Az Powershell module.
Deprecation Timeline
The full details are listed in the change announcement, however in summary:
The three modules will continue to work with minimal investment, apart from security updates. Depending on the status of Azure AD API, some cmdlets might stop working after June 30, 2023.
The Microsoft Graph PowerShell SDK continues to be where all our current and future PowerShell investments are being made, and we encourage you to continue migrating to Microsoft Graph PowerShell SDK.
In other words, migrating to Microsoft Graph Powershell is the only supported way forward.
Microsoft provide additional resources in their migration FAQ.
The dreaded Admin Consent
The biggest difference from prior Powershell modules (and in fact from Azure CLI and Az Powershell as well) is the Admin consent requirement.
For background, refer to the Microsoft Graph Powershell Getting Started.
The Getting Started guide shows how to initially connect with Microsoft Graph Powershell and use the cmdlets. In essence the workflow is:
- Use Find-MgGraphCommand to discover the required permissions to run the desired command
- Connect with the required scopes
- Consent if needed
That last step is the stumbling block. Consider the examples below:
Example 1
The cmdlet given in the Get Started guide is Get-MgUser and that can be used with non-admin permission set of User.ReadBasic.All.
What if we want to get information about something else?
Get-MgServicePrincipal requires permission scopes that all need Admin consent.
If you have Reader access and can directly see the Application and Service Principal details in the portal, you cannot query these via MS Graph Powershell without Admin consent.
Notably, you can bypass this artificial limitation by simply using Az Powershell's Get-AzADApplication instead, but this workaround is only valid for use cases that overlap, and assumes that Microsoft won't deprecate Az Powershell next.
Example 2
The above example shows that some commands in MS Graph Powershell require Admin consent even if permissions to query that information are otherwise available.
Now consider that not even User consent is a generally serviceable requirement.
By default, users in AzureAD are allowed to consent to applications.
Due to the massive security implications of OAuth2 illicit consent grant, one of the first things a security administrator will do is disable User consent and force Admin approval.
As such, if your tenant has even the basic protections against illicit consent grants, you will need Admin approval to consent to a user level permission.
As a result, even consenting to User.ReadBasic.All to use Get-MgUser is impossible with administrator approval.
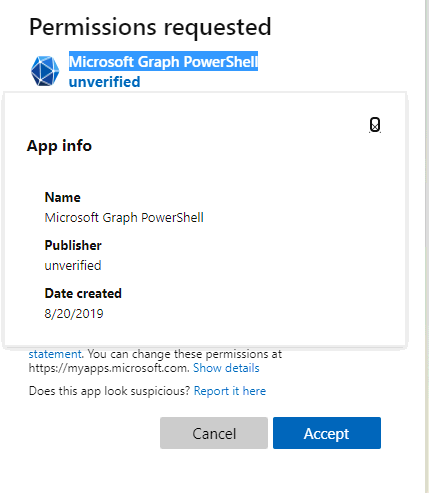
What's worse is that the consent dialog shows the application name for Microsoft Graph Powershell as "unverified"!
This Github issue shows that this has been the case since 2020 (and is the source for the above image).
Would you expect a busy administrator to approve a user's consent request to an application called "unverified"?
Thoughts
This is quite unexpected and in my opinion provides horrible usability, as well as violating least privilege (at least from the perspective that a Reader-role user should not need Admin consent in order to use their existing Reader permissions).
Microsoft themselves state that "Uses least privilege: Microsoft Graph PowerShell permissions are not pre-authorized and users must perform one-time request for app permissions depending on their needs."
Microsoft's Response
While I have been unable to find an official statement on Microsoft Docs, this Github issue has been an informative read.
As far as I can surmise, there are Microsoft engineers who have a similar take on this to myself, but that is not the prevailing viewpoint.
Hence the (in my opinion needless) admin consent situation shows no indication of changing. The most informative comments I've been able to find are on the Github page mentioned above.
I can only hope that Microsoft change the current design as in its current state MS Graph Powershell is unusable to anyone who isn't a tenant admin already.
Reader-privilege staff in large organisations, staff in organisations that outsource their MS365 admin, or consultants that have least-privilege roles as standard practice, and others in similar situations will be potentially left without the ability to query AzureAD programmatically.
Update
Since originally writing this, I've been advised that Microsoft has extended the initial deprecation deadline of June 2023, to March 2024.
More details in the announcement.
I hope this gives more time for issues like the Admin consent to be addressed.